Microsoft Cloud Adoption Framework
The Microsoft Cloud Adoption Framework for Azure is a full lifecycle framework that enables cloud architects, IT professionals, and business decision makers to achieve their cloud adoption goals. It provides best practices, documentation, and tools that help you create and implement business and technology strategies for the cloud.
Following best practices for the Cloud Adoption Framework allows your organization to better align business and technical strategies and ensure success.
The Cloud Adoption Framework brings together cloud adoption best practices from Microsoft employees, partners, and customers. The framework provides tools, guidance, and narratives. The tools it includes help you shape your technology, business, and people strategies to achieve the best business outcomes possible through your cloud adoption effort. Use the following table to review the guidance for each methodology.
The main objective of this minihack is to guide you through the process to understand the basics of CAF and show you how to prepare your cloud environment to bring your workloads into your cloud using the Azure Landing Zone Accelerator.
Azure landing zones are the output of a multi-subscription Azure environment that accounts for scale, security governance, networking, and identity. Azure landing zones enable application migration, modernization, and innovation at enterprise-scale in Azure. These zones consider all platform resources that are required to support the customer’s application portfolio and don’t differentiate between infrastructure as a service or platform as a service.
The azure landing zone conceptual architecture represents the strategic design path and target technical state for your azure environment.
The landing zone accelerator is a ARM Template build by Microsoft expert that uses the Enterprise-Scale architecture which allows customers to start with foundational Landing Zones that support their application portfolios, regardless of whether the applications are being migrated or are newly developed and deployed to Azure. The architecture can scale alongside the customer’s business requirements regardless of the scale point. We will be using the Azure without hybrid connectivity template but in this repository, we provide you will all the templates that represent all the different scenarios composed by us using ARM templates.
Customer situation
The BAM Academy is a Global educational institute for minorities with headquarters in San José, Costa Rica with 9 locations around the globe located in America, Europe and Africa. They promote free and equal access to quality education for all minorities.
Their environment was developed by volunteers and it is disorganized, because most of the volunteers leave after the default period of 6 months. There current environment is based on a couple of old servers that were donated to the organization running Hyper-V with 3 environments Production, QA/Test and Development. During the year the environment is handle by 3 employees (the security and identity expert, the networking expert and the one that does it all).
The new leader of IT reached out to Microsoft Philanthropy and requested their support in order to do a reorganization of the architecture and infrastructure.
Microsoft group granted them with an Azure subscription for 3 years to allow them to move their current environment into the Azure and support from CSAs to Migrate their infrastructure into the cloud to help them on their journey to empowered others to achieve more.
When asked for a diagram this is the only one that were able to provide for an old implementation of SharePoint and they also mention that some of the old servers need to remain on-premise because of some old application that cannot be migrated to the cloud.

Let’s become the Microsoft architects and initiate a whiteboard design session to draft their new environment into the cloud.
Whiteboard session (Tech@Scale)
This should be the first stop in your destination of your cloud adoption journey. The architecture we will designed is intended to help any customer and organization to operate successful cloud environments that drive your business while it maintains the best practices for security and governance.
This conceptual architecture represents scale and maturity decisions based on a wealth of lessons learned and feedback from customers who have adopted Azure as part of their digital estate.
We know that your specific implementation will vary, as a result of specific business decisions, specific requirements or existing investments in tools that need to persist in your cloud environment, but we are sure that understanding this conceptual architecture will help set a direction for the overall approach your organization will take to designing and implementing a landing zone.
Step 1. Whiteboard and Landing Zone assessment
So, let’s dive into the whiteboard and use the Azure Landing Zone assessment to review your platform readiness to adoption can begin, assess your plan to create a landing zone to host the BAM Academy workloads you plan to build or migrate to the cloud.
- Note: You can download or use the digital online whiteboard from the following link: Digital Online Whiteboard App – Microsoft Whiteboard.
Step 2. Build the architecture
Once you have your initial questionnaire and whiteboard completed, we will use that information to build the landing zone architecture.
Let’s use the default template and then we will review the environment of BAM Academy.
- Note: You can download the reference architecture from here.
Hands-On lab
Exercise 1: Implement Azure landing zone accelerator
Duration: 35 minutes
Synopsis: In this exercise, attendees will simulate the implementation of the landing zone template for Azure without hybrid connectivity which is ideal for customers who want to start with Landing Zones for their workloads in Azure, where hybrid connectivity to their on-premises datacenter is not required from the start.
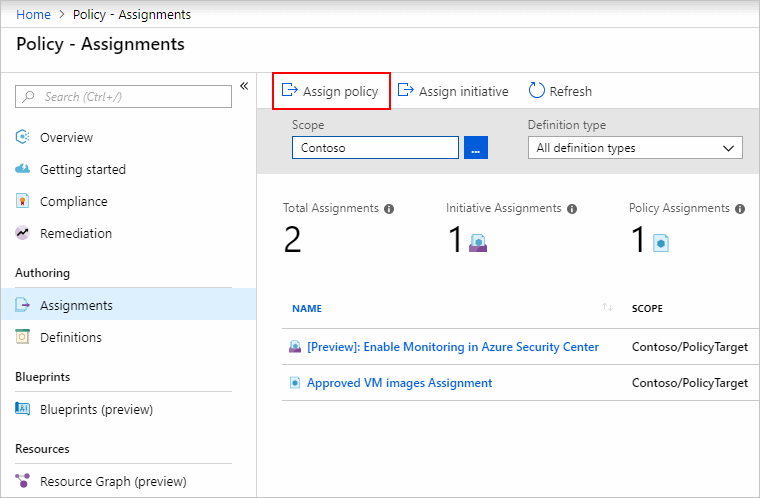
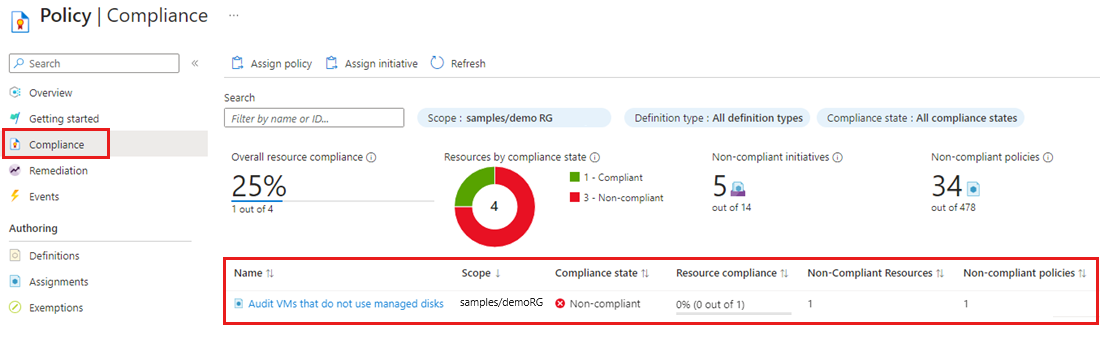
In a private browser, navigate to your Azure portal (https://portal.azure.com) and login using the accounts provided by the trainer. In a separate tab lets go to Deploy Enterprise-Scale Architecture templates page and select the ARM template that best adjust to the BAM Academy requirements and design. Once you read the general information lets click on Deploy to Azure, this will load the deployment experience in the Azure portal into the BAM-Academy Azure tenant. On the first page, select the Region. This region will primarily be used to place the deployment resources in an Azure region, but also used as the initial region for some of the resources that are deployed, such as Azure Log Analytics and Azure automation. Provide a prefix that will be used to create the management group hierarchy and platform resources, and select if you would use dedicated subscriptions or a single subscription for platform resources (please note that dedicates subscriptions are recommended). For this scenario, select Dedicated. On the Platform management, security, and governance blade, you will configure the core components to enable platform monitoring and security. The options you enable will also be enforced using Azure Policy to ensure resources, landing zones, and more are continuously compliant as your deployments scales and grows. To enable this, you must provide a dedicated (empty) subscription that will be used to host the requisite infrastructure. Please note that if you enable the “Deploy Azure Security Center and enable security monitoring for your platform and resources” option, you will need to provide an email address to get email notifications from Azure Security Center. You can choose to bootstrap your CI/CD pipeline (GitHub with GitHub actions). Provide your GitHub user/org name, the preferred name of the GitHub repository that is to be created, as well as the PA token that the deployment will use to create a new repository and discover the Enterprise-Scale deployment ARM templates and merge them into your main branch. 1.1.1 To create a PA token, follow the instructions here: https://docs.github.com/en/github/authenticating-to-github/creating-a-personal-access-token 1.1.2 Ensure the PA token has the following permissions: For Microsoft employees who are enrolled into the Azure GitHub organization, you must also authorize the PA token to this Org! 1.2 Lastly, a Service Principal is required for Git to authenticate to – and be authorized to your Azure tenant. You can either use an existing Service Principal or create a new one. The Service Principal will be granted Owner permission on the top level Management Group that gets created. 1.2.1 If using an existing Service Principal, ensure you have the client secret as this must be provided as the Password for the service principal and confirm it has the right level of permission. 1.2.2 If creating a new Service Principal, select “Create New” and click on Make selection” and the portal will open a new blade for app registration Once the App has been registered, you must explicitly create a new secret. Make sure to note down the “Value” of the new client secret. The default API Permissions for this App are “User.Read”, as depicted below: After copying the secret, go to “Enterprise-Scale Landing Zones” (in the upper left) to return to the deployment. At this point, paste the client secret value of the newly created client secret from a few step above into the Password field. On the Network topology and connectivity blade, you will configure the core networking platform resources, such as hub virtual network, gateways (VPN and/or ExpressRoute), Azure Firewall, DDoS Protection Standard and Azure Private DNS Zones for Azure PaaS services. To deploy and configure these network resources, you must select a network topology (for this scenario, select either “Hub and spoke with Azure Firewall” or “Hub and spoke with your own third-party NVA”), provide the address space to be assigned to the hub virtual network, select an Azure region where the hub virtual network will be created and provide a dedicated (empty) subscription that will be used to host the requisite infrastructure. For this example, we will select the “Hub and spoke with Azure Firewall” network topology. Depending on your requirements, you may choose to deploy additional network infrastructure for your Enterprise-Scale landing zones platform. The optional resources include: On the Identity blade you can specify if you want to assign recommended policies to govern identity and domain controllers. If you decide to enable this feature, you do need to provide an empty subscription for this. You can then select which policies you want to get assigned, and you will need to provide the address space for the virtual network that will be deployed on this subscription. Please note that this virtual network will be connected to the hub virtual network via VNet peering. You can optionally bring in N number of subscriptions that will be bootstrapped as landing zones, governed by Azure Policy. You indicate which subscriptions will be bootstrapped as landing zones with a virtual network deployed and connected to the hub virtual network for corp connectivity. Virtual networks on these subscriptions will be connected to the hub virtual network using VNet peering, and if you deployed and enabled Azure Firewall as DNS proxy, DNS settings on these VNets will be configured with the Azure Firewall private IP address. You can also indicate which subscriptions you would like to be bootstrapped as landing zones but without corp connectivity. Finally, you can select which policy you want to assign broadly to all of your landing zones. As part of the policies that you can assign to your landing zones, the Enterprise-Scale Landing Zones deployment experience will allow you to protect your landing zones with a DDoS Standard plan, and for corp connected landing zones, you will have the option to prevent usage of public endpoints for Azure PaaS services as well as ensure that private endpoints to Azure PaaS services are integrated with Azure Private DNS Zones. Review + Create page will validate your permission and configuration before you can click deploy. Once it has been validated successfully, you can click Create Note: The deployment will take around 35 minutes. For this reason we will use the already preconfigure landing zone space. Duration: 45 minutes Synopsis: In this exercise, we will review the implementation we did in exercise 1. Once the implementation is completed you should be able to view any management group you have a direct or inherited Azure role on. Log into the Azure portal. Select All services > Management groups. The management group hierarchy page will load. This page is where you can explore all the management groups and subscriptions you have access to. Selecting the group name takes you to a lower level in the hierarchy. The navigation works the same as a file explorer does. To see the details of the management group previously created, select the “bam-“ management group and expand it. Duration: 30 minutes Synopsis: In this exercise, will create a policy and identify non-compliant resources. In this quickstart, you create a policy assignment and assign the Audit VMs that do not use managed disks policy definition. Launch the Azure Policy service in the Azure portal by selecting All services, then searching for and selecting Policy. Select Assignments on the left side of the Azure Policy page. An assignment is a policy that has been assigned to take place within a specific scope. Select Assign Policy from the top of the Policy – Assignments page. On the Assign Policy page, set the Scope by selecting the ellipsis and then selecting either a management group or subscription. Optionally, select a resource group. A scope determines what resources or grouping of resources the policy assignment gets enforced on. Then use the Select button at the bottom of the Scope page. This example uses the Contoso subscription. Your subscription will differ. Resources can be excluded based on the Scope. Exclusions start at one level lower than the level of the Scope. Exclusions are optional, so leave it blank for now. Select the Policy definition ellipsis to open the list of available definitions. Azure Policy comes with built-in policy definitions you can use. Many are available, such as: For a partial list of available built-in policies, see Azure Policy samples. Search through the policy definitions list to find the Audit VMs that do not use managed disks definition. Select that policy and then use the Select button. The Assignment name is automatically populated with the policy name you selected, but you can change it. For this example, leave Audit VMs that do not use managed disks. You can also add an optional Description. The description provides details about this policy assignment. Assigned by will automatically fill based on who is logged in. This field is optional, so custom values can be entered. Leave policy enforcement Enabled. For more information, see Policy assignment – enforcement mode. Select Next at the bottom of the page or the Parameters tab at the top of the page to move to the next segment of the assignment wizard. If the policy definition selected on the Basics tab included parameters, they are configured on this tab. Since the Audit VMs that do not use managed disks has no parameters, select Next at the bottom of the page or the Remediation tab at the top of the page to move to the next segment of the assignment wizard. Leave Create a Managed Identity unchecked. This box must be checked when the policy or initiative includes a policy with either the deployIfNotExists or modify effect. As the policy used for this quickstart doesn't, leave it blank. For more information, see managed identities and how remediation security works. Select Next at the bottom of the page or the Non-compliance messages tab at the top of the page to move to the next segment of the assignment wizard. Set the Non-compliance message to Virtual machines should use a managed disk. This custom message is displayed when a resource is denied or for non-compliant resources during regular evaluation. Select Next at the bottom of the page or the Review + Create tab at the top of the page to move to the next segment of the assignment wizard. Review the selected options, then select Create at the bottom of the page. You're now ready to identify non-compliant resources to understand the compliance state of your environment. Select Compliance in the left side of the page. Then locate the Audit VMs that do not use managed disks policy assignment you created. If there are any existing resources that aren't compliant with this new assignment, they appear under Non-compliant resources. When a condition is evaluated against your existing resources and found true, then those resources are marked as non-compliant with the policy. The following table shows how different policy effects work with the condition evaluation for the resulting compliance state. Although you don't see the evaluation logic in the Azure portal, the compliance state results are shown. The compliance state result is either compliant or non-compliant. Note The DeployIfNotExist and AuditIfNotExist effects require the IF statement to be TRUE and the existence condition to be FALSE to be non-compliant. When TRUE, the IF condition triggers evaluation of the existence condition for the related resources. Task 1 Lets deploy the template
Note: Your subscription may not be set up with the Standard tier
Deployment locations

Enterprise-Scale core setup
Platform management, security, and governance


Platform DevOps and Automation
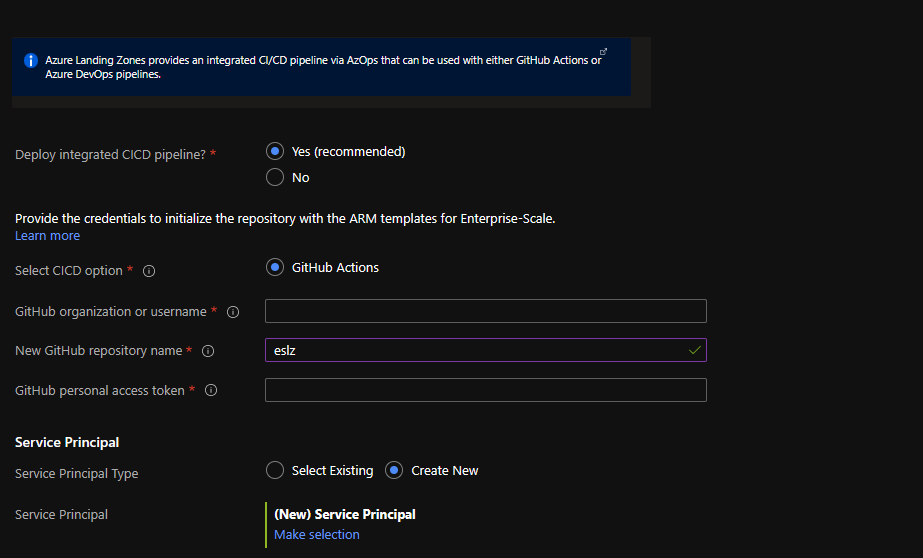












Network topology and connectivity


Identity

Landing zone configuration

Review + create

Exercise 2 – Lest review the implementation
Task 1: Review the Management groups
Exercise 3: Lets identify non-compliant resources
Task 1: Lets create a policy assignment



Task 2: Let's identify non-compliant resources for this new policy
Resource State
Effect
Policy Evaluation
Compliance State
New or Updated
Audit, Modify, AuditIfNotExist
True
Non-Compliant
New or Updated
Audit, Modify, AuditIfNotExist
False
Compliant
Exists
Deny, Audit, Append, Modify, DeployIfNotExist, AuditIfNotExist
True
Non-Compliant
Exists
Deny, Audit, Append, Modify, DeployIfNotExist, AuditIfNotExist
False
Compliant
Additional references
| Description | Links |
| MS Learn Azure business value course module on CAF | https://aka.ms/adopt/learn/bizvalue |
| Governance Guides |
https://aka.ms/adopt/gov/journey |
| Migration Guide | https://aka.ma/adopt/migration/guide |
| CAF DOCS home page | https://aka.ms/adopt/overview |
| Landing zone docs page | https://aka.ms/adopt/landingzone |
